
The heeled hacker's toolkit.
Posted on 08/24/2015 4:12:58 AM PDT by markomalley
Mildly nsfw A Chinese hardware hacker has built a penetration testing toolkit built into high-heeled shoes.
The WiFi-popping platforms were forged in a 3D printer and contain spacing so that hacking hardware can be hidden to bypass strict security checks in place at datacentres and the like and later retrieved.
The hacker and pen-tester, who goes by the handle "SexyCyborg", showcases the heels she dubs Wu Ying shoes, named after the famed "shadowless kick" that Chinese folk hero Wong Fei Hung used to distract opponents.
The hacker showcased the shoes in a post (somewhat NFSW) showing how a router, backup battery, and lock-picking set can be concealed from security guards while on red team penetration tests.
"With my shadowless shoes I distract the target with my upper body and they don’t see the real danger on my feet," she writes.
"Each shoe has a drawer that can be slid out without my having to take the shoes off [which] can be customised for various payloads.
SexyCyborg says "... my right shoe contains a pen testing drop box which is a wireless router running OpenWRT with a built in rechargeable battery that could either be left running inside the shoe (for war-walking, wifi sniffing and logging) or could be removed and plugged into a convenient open network jack [gaining] gain remote access anytime via SSH tunnel."
(image snipped)
Social engineering penetration testers have various tricks they use to gain access to restricted areas. Staff access badges are frequent targets for cloning as they dangle from waist belts, while polished silver-tongue swindling is a staple for conning helpful employees into opening doors.
She says bringing hacking tools into a security facility by way of a handbag is too conspicuous while policy typically demands mobile phones are left outside.
 The heeled hacker's toolkit. |
Her skimpy outfit is also a tactical decision; "My typical clothing does not leave room to hide anything, but that’s all the more reason they would not be suspicious of me," she says.
The Chinese hacker installed the OpenWRT firmware on a TL-MR10U router concealed in a cavity within the heel that runs Wispi and Jasager. Those tools can help the heeled hacker set up rogue access points that trick employees into punching in their enterprise credentials into fake phishing login pages.
"Wispi and pen-test drop boxes should of course should only be experimented with at home for educational purposes; while it’s good to know about this stuff, always obey your local laws," she says.
Hackers can "go all out" and run Kali and or PwnPi on a Raspberry Pi but the pen tester warns the shoes may start to get heavy.
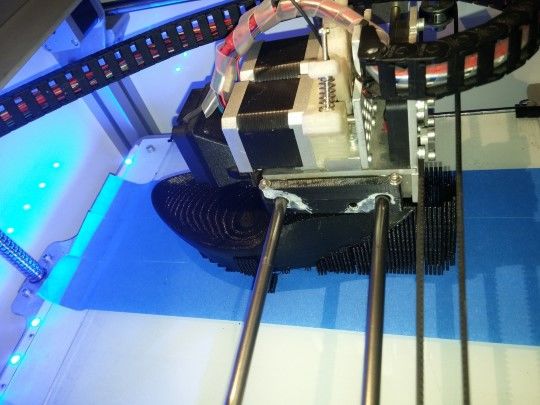 The 3D printer in action. |
The hacker has released the 3D-printer blueprints for enterprising hackers to follow and says the heels are strong and safe to wear.

Sounds like she needs to be found and stopped.
Looks like she has some added volume up top that could also conceal items.
I volunteer to check
How dare she desecrate shoes, and with that bad blob job too!
While dressing like that may keep people from checking her shoes too closely, it would have the disadvantage that every bored security officer would be checking her out on video monitors. She’d have a tough time staying out of surveillance in a building with any security.
To be fair, most inside threats come from people with high-level access to systems already. Specifically, contractors and consultants with administrative access to systems can plant all manner of rootkits and trojans, and with American companies still Hell bent on outsourcing IT to India, Russia, and Mexico, it should be no surprise to most of us that our data is about as safe as a dollar bill stuffed in a mattress.
Most data centers I’ve worked in have annex staff/operations areas with open and often active network ports. If they don’t have some sort of NAP or NAC product running on their network or are otherwise diligent about turning off network ports at the switch, it would be pretty easy to pull this off without much effort.
Actually, a dollar bill stuffed in your matress is about as safe as it gets these days.
My experience has been similar, although I never probed the staff area to see what could be compromised.
I did use a secure hosting facility once that had pretty phenomenal security. When I was working on my servers, if I needed something, a quick wave to the nearest camera and someone would appear. Kinda weird knowing you’re being monitored that closely even when doing mundane tasks, but that’s what we were spending the big bucks for.
I have never thought the executive lure to source code overseas or hire a bunch of H1s was smart.
They do it to increase their bonuses, but the compromise their systems.
It’s not just the potential for compromise.
In my experience, while the coders are generally good enough to get the code down, they lack documentation skills and are often very sloppy coders.
As far as admins, don’t get me started. I’ve been a Windows server admin for the better part of 15 years, and I’ve yet to find an admin from an Indian contracting agency who knows any more than just how to reboot a Windows server and do basic functionality checking. Even Microsoft certifications don’t equate to practical knowledge.
I don’t care how many attributes a pair of shoes has. I ditched all my high heels when I retired and will never put on another pair for any reason. Ditto for panty hose.

Well those definitely aren’t stilletos and I bet they may not function very well from a practical standpoint. I can see the heels working themselves loose as she’s walking and the goodies spilling out. looks like there’s just your typical lockpicking tools, a USB drive, mini-router, and backup battery; basically just tools to get you access then plug in a USB drive to extract data or a small router to semdvthe data to another remote device. Not nearly the type of tools you would need for real world hacking onsite. If they have a keycard system, camera’s or any biometric key systems that kit won’t do squat. She might be able to hack ner next door neighbor or a small business’ computer. Just hype for a novelty item she’ll probably try to sell online later.
Photo looks photoshopped big time. CG hair, boobs, and eyes...
Old silver coins maybe.
If she dressed like that in the last datacenter I worked in she would suffer from severe hypothermia before gaining access. Seriously though, anyone dressed like that in a DC would get a lot of attention because it’s wildly innapropriate.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.