Posted on 10/20/2014 5:45:33 AM PDT by Citizen Zed
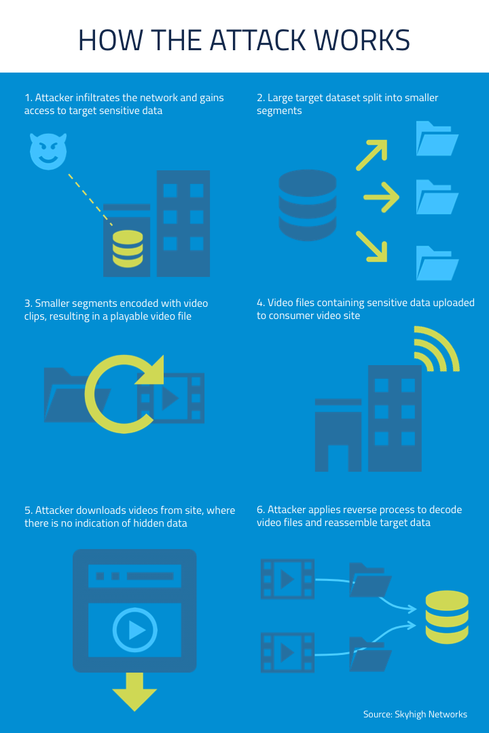
In this attack, once hackers gained access to sensitive data stored by the company on the network, they split the data into compressed files of identical sizes, similar to how the RAR archive format transforms a single large archive into several smaller segments. Next, they encrypted this data and wrapped each compressed file with a video file. In doing so, they made the original data unreadable and further obscured it by hiding it inside a video file, a file format where it's not unusual to see multi-gigabyte file sizes. The video files containing stolen data played normally. What was unusual is that each file was an identical size, which is anomalous since encoded videos are usually not the exact same file size.
(Excerpt) Read more at darkreading.com ...

/mark

does this mean I can’t torrent tv shows now?
This article is like describing a bank robbery by how the criminals laundered the money.
If you work in ITSEC for a corporation, do egress filtering and logging on all video and compression formats.
I’m available for consulting. :-)
Well said. Which tools do you need to perform these attacks even if the box is compromised?
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.