Posted on 10/19/2011 2:08:07 PM PDT by blam
Major Security Firms Detect New Trojan Capable Of Disrupting Power Plants, Oil Refineries and Other Critical Infrastructure Networks
Mac Slavo
October 19th, 2011

In our October 7, 2011 report There Have Been Intrusions, we noted that DHS Undersecretary Greg Shaffer warned that hackers and foreign governments are “knocking on the backdoor” of the networked systems which connect everything from infrastructure grid control systems to financial networks.
It now appears that our interconnected smart grid is actively under attack, as evidenced by a new Stuxnet-style trojan that has been detected by major cyber security leaders Symantec and McAfee. Much like its predecessor, the trojan dubbed “Duqu” is designed to infilitrate the networks that control everything from power production facilities to oil refineries. It is not yet clear exactly how the trojan operates, what its intended purpose is, or who designed it (though it is believed that the code for Duqu and Stuxnet likely originated with U.S. intelligence agencies). Both Symantec and McAfee continue to investigate the threat:
Security researchers have detected a new Trojan, scarily similar to the infamous Stuxnet worm, which could disrupt computers controlling power plants, oil refineries and other critical infrastructure networks.
The Trojan, dubbed “Duqu” by the security firm Symantec, appears, based on its code, to have been written by the same authors as the Stuxnet worm, which last July was used to cripple an Iranian nuclear-fuel processing plant.
…
“Duqu shares a great deal of code with Stuxnet; however, the payload is completely different,” researchers for the security firm Symantec wrote on its Security Response blog.
Instead of directly targeting the SCADA system, Duqu gathers “intelligence data and assets from entities, such as industrial control system manufacturers, in order to more easily conduct a future attack against another third party. The attackers are looking for information such as design documents that could help them mount a future attack on an industrial control facility.”
“Duqu is essentially the precursor to a future Stuxnet-like attack,” the researchers added.
Source: Fox News
You may recall that Stuxnet was so advanced that it crashed the physical centrifuges used to enrich uranium in Iran’s nuclear facilities. Stuxnet did this by exploiting software and hardware vulnerabilities, essentially reporting to Iranian research facility engineers that everything was functioning properly by controlling the software interface, while in the background it sent centrifuges spinning out of control to the point of hardware failure.
Duqu, which is apparently a similar piece of advanced code with a slightly different modus operandi, is not yet completely understood, but like Stuxnet in Iran, it is now actively functioning inside of critical infrastructure systems gathering information. To what end? The answer to that question may remain elusive until it’s too late.
In reportedly unrelated news, the Department of Homeland Security, in an unclassified National Cybersecurity and Communications Integration Center Bulletin (pdf), has issued warnings about the hacking group Anonymous and the possibility that they are becoming increasingly capable of targeting advanced Industrial Control Systems (ICS):
(U//FOUO) The information available on Anonymous suggests they currently have a limited ability to conduct attacks targeting ICS. However, experienced and skilled members of Anonymous in hacking could be able to develop capabilities to gain access and trespass on control system networks very quickly. Free educational opportunities (conferences, classes), presentations at hacker conferences, and other high profile events/media coverage have raised awareness to ICS vulnerabilities, and likely shortened the time needed to develop sufficient tactics, techniques, and procedures (TTPs) to disrupt ICS. Control system exploits are released in common penetration testing software such as Metasploit release 4.0 that can be directly used with novice level skills in hacking and little to no background in control systems. Common packet inspection tools such as WireShark and Netmon have improved to the point where industrial protocols are supported minimizing the effectiveness of security-by-obscurity. In addition, there are control systems that are currently accessible directly from the Internet and easy to locate through internet search engine tools and applications. These systems could be easily located and accessed with minimal skills in order to trespass, carry out nefarious activities, or conduct reconnaissance activities to be used in future operations.
(U//FOUO) Anonymous has recently called on their members to target energy companies based on “Green Energy” initiative performance. This targeting could likely extend beyond Anonymous to the broader hacktivist community, resulting in larger-scope actions against energy companies. Asset owners and operators of critical infrastructure control systems are encouraged to engage in addressing the security needs of their control system assets.
Curiously, the Duqu trojan doesn’t seem to have originated from individual hackers or hacking groups, or foreign intelligence services. Rather, like Stuxnet, the virus was likely written under control and/or guidance of U.S. intelligence, possibly in collaboration with Israeli intelligence.
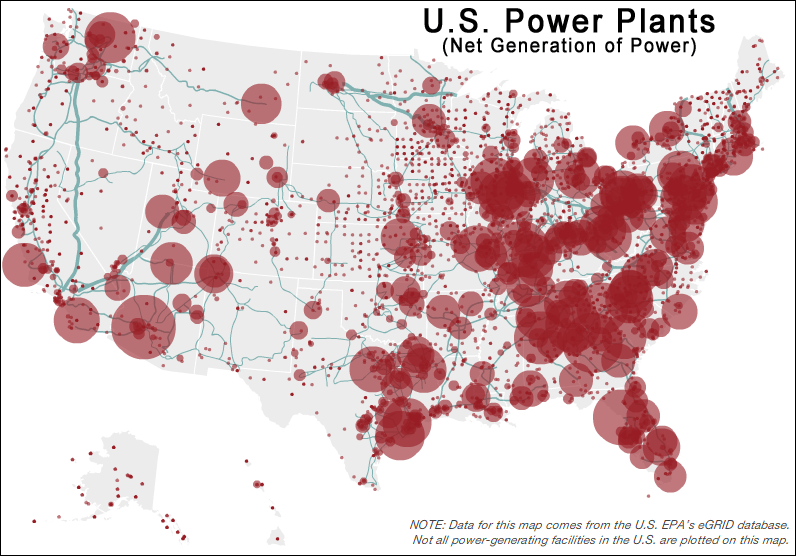
While DHS has issued warnings about Anonymous and other hacking groups potentially attacking the grid, someone – and it’s likely not a lone hacker or the Anonymous hacking group – is actively involved in probing for vulnerabilities in our infrastructure control systems. These are the systems that monitor and control our electricity, water supplies, gas pipelines, oil refineries, financial exchanges, and even certain military operations.
There seems to be no immediate danger at this time, as the Duqu trojan is reportedly gathering intelligence, as opposed to actively attempting to bring down the systems via a hardware style attack like Stuxnet.
But once it acquires all of the necessary information, such as personnel access codes, security certificates and a mapped layout of a particular grid infrastructure, it wouldn’t take much to take things to the next level.
Imagine for a moment the effect of an attack on major refining operations, cascading electrical outages, urban water purification systems that added excessive chemicals to water supplies, or the massive flooding that might result if a dam were compromised.
Or, consider that the U.S. drone fleet was recently attacked by an unknown trojan or malware, which was logging access commands and passwords for high security military systems. What would happen if an enemy of the people of the United States gained access to our entire drone fleet, weapons systems and all?
The possibilities for damage via compromised infrastructure systems would be nothing short of a digital apocalypse, with the potential to adversely affect the lives of tens of millions of unsuspecting Americans virtually overnight.
Interesting. Check out this link: http://www.f-secure.com/weblog/archives/00001393.html
This has been simmering since around since 2008, but seems to be exactly this type of thing. Very sophisticated, yet simple. Encrypted so it doesn’t have a footprint, residing in sectors on your drive that your OS doesn’t recognize, etc.
This link: http://www.ted.com/talks/mikko_hypponen_fighting_viruses_defending_the_net.html
is also interesting...I really detest the TED people, they are as liberal as the day is long, but this guy, Mikko Hypponen relates some very interesting stuff on viruses, malware and Internet crime.
Very interesting...I highly recommend it, even with the socialist bent at the end where he suggests getting jobs for programmers who haven’t gone criminal yet...(haha, what a laugher THAT idea is)
I worked in the Microsoft operating system development team for several years. Part of the fun was working with smart foreign nationals from all kinds of interesting places. Sometimes when you got to know them well enough to ask what they did before they came to the US, you could get quite a shock. For example, an ICBM launch officer from USSR. I’ve often wondered how you could ever vet these people adequately.
Heck, I figured I might as well paste the whole thing in from the first link:
News broke out earlier this year (My Note: this was March 2008) of a new breed of rootkit using techniques never before seen in modern malware. The most notable of them is the fact that the rootkit replaces the infected system’s Master Boot Record (MBR).
The MBR is the first physical sector of the hard drive and contains the first code loaded and executed from the drive during the boot process.
In the competition between rootkits and rootkit detectors, the first to execute has the upper hand. And you can’t execute earlier than from the MBR. Of course, MBR viruses used to be very common in the DOS days, 15 years ago or so. But this is 2008.
This new Windows MBR rootkit launches itself very early during the Windows startup process without requiring any registry or file modifications. In fact, it is quite surprising that it’s possible to write to the MBR from within Windows to begin with.
The MBR rootkit — known as “Mebroot” — is very advanced and probably the stealthiest malware we have seen so far. It keeps the amount of system modifications to a minimum and is very challenging to detect from within the infected system.
Below are some details about the MBR rootkit’s stealth features:
The ntoskrnl.exe module hook that executes the kernel-mode downloader payload is set to the nt!Phase1Initialization function which resides in the INIT section. This means that after the system has initialized the section is wiped out from memory and no sign of the hook is any longer present.
The rootkit stores data that’s required to survive reboots in physical sectors instead of files. This means that the data, including the real payload, is not visible or in any way accessible to normal applications. Therefore the rootkit does not have to hook the normal set of interfaces to keep them hidden.
The MBR is the rootkit’s launch point. Therefore it doesn’t need to make any registry changes or to modify any existing startup executables in order to launch itself. This means that the only hooks it needs to make are used to hide and protect the modified MBR. Essentially this means that the rootkit hooks only two DWORDs from the disk.sys driver object which is shown in the picture below.
Another interesting feature of the MBR rootkit that has not received very much public discussion is its networking layer and firewall bypassing capabilities. One reason for this might be that this part of Mebroot’s code is heavily obfuscated and time consuming to analyze.
It is known that the rootkit’s main purpose is to act as an ultimate downloader. To be stealthy and effective it is essential that the rootkit does not trigger nor is blocked by personal firewalls. It is able to achieve this by operating in the lowest parts of the NDIS layer just above the physical hardware.
Only a single DWORD is hooked at all times from the NDIS internal structures. To send packets the rootkit uses the SendPacketsHandler function implemented by the actual hardware specific driver.
The rootkit uses its own unmodified versions of NDIS API functions it needs to operate. This has been done before by some malware, such as Rustock and Srizbi. However, what we have not seen before is the fact that the MBR rootkit uses a “code pullout” technique to only load the relevant code from the ndis.sys driver instead of loading the whole ndis.sys driver as its private module into memory.
This means that the memory fingerprint of the malware is smaller and there are no additional modules loaded into the system address space which might trigger some forensic tools.
This malware is very professionally written and produced. Which of course means it’s not written for fun. Initial samples from December 2007 and January 2008 were at beta stage. Now it appears that the malware is fully-baked and more active distribution has begun. During the weekend our Security Lab started to receive information about multiple drive-by exploit sites spreading the latest version. (However, at the moment these attacks cannot be considered as widespread.)
The actual site hosting the exploit code utilizes the following exploits:
Microsoft Data Access Components (MDAC) Function vulnerability (MS06-014)
AOL SuperBuddy ActiveX Control Code Execution vulnerability (CVE-2006-5820)
Online Media Technologies NCTsoft NCTAudioFile2 ActiveX Buffer Overflow (CVE-2007-0018)
GOM Player “GomWeb3” ActiveX Control Buffer Overflow (CVE-2007-5779)
Microsoft Internet Explorer WebViewFolderIcon setSlice (CVE-2006-3730)
Yahoo! JukeBox datagrid.dll AddButton() Buffer Overflow
DirectAnimation.PathControl KeyFrame vulnerability (CVE-2006-4777)
Microsoft DirectSpeechSynthesis Module Remote Buffer Overflow
Proof of concept code for two of the exploits was publicly disclosed just less than a month ago.
The downloaded payloads seem to clearly target online banking and other financial systems.
We detect the latest MBR rootkit variant as Backdoor.Win32.Sinowal.Y.
The exploit site is currently resolving to an IP address of 216.245.195.114 and seems to still be active.
Thanks for the links. The MBR replacement scheme looks really scary to me. I’m not sure how you deal with that.
And the TED video was quite good. If you watched closely you would have heard him say that they can now embed malware in a .jpg. Click on the .jpg and infect your computer. Yikes.
I like TED despite it’s obvious leftist tilt. Very professionally done. Actually a valuable resource.
NOBODY seems to know what to do or how to deal with this particular kind of thing. (Perhaps some more knowledgeable person on this thread might know a bit more...)
I found that paucity of follow-up information a little disturbing. The key verbiage from that website I thought was this:
The rootkit stores data that’s required to survive reboots in physical sectors instead of files. This means that the data, including the real payload, is not visible or in any way accessible to normal applications. Therefore the rootkit does not have to hook the normal set of interfaces to keep them hidden.
The MBR is the rootkit’s launch point. Therefore it doesn’t need to make any registry changes or to modify any existing startup executables in order to launch itself. This means that the only hooks it needs to make are used to hide and protect the modified MBR.
Why can’t they make a removal/replacement software to run during bios pre-boot? Seems likely to me, that if you can detect the malware, you can remove it. Such as off a flash drive, cd, or external hard drive?
While initial reports suggested Israel, other reports suggested China or even the United States-—
I dunno, I have a hard time thinking the U.S. would name such a thing as Duqu..but that’s just me..
I get the impression that part of the problem is...you cannot detect it.
Right, I read that, but that was back in 2008, and if I’m reading correctly this is the same type of malware used years ago when dos was prevalent in Windows OS. So it’s been about 3 years since this article was written and still undetectable? They know enough to know that it’s infected infrastructure software throughout the US but they can’t detect it? I don’t buy it.
Doesn't that sound more 'Chinese-like'?
Not dangerous? Really? Information is power. One access code and you're inside and capable of doing anything.
Symantec stinks. Does nothing but crash and slow things down. Never again.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.