Posted on 03/07/2017 6:16:30 PM PST by Swordmaker
Although Google’s Android dominates the worldwide smartphone market, the CIA concentrated on Apple’s iOS because of its popularity among global elites, WikiLeaks reports.
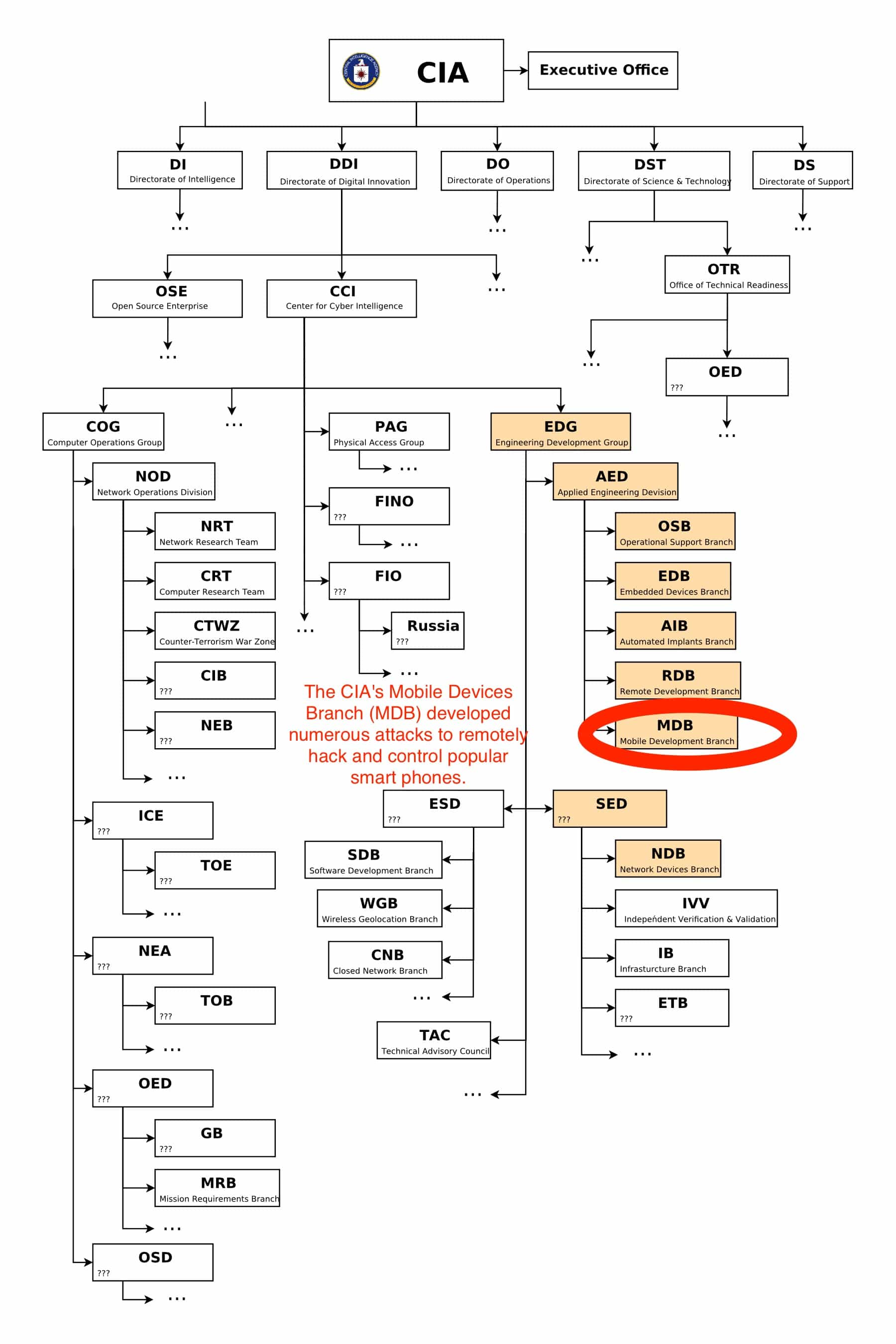
The huge trove of leaked CIA documents, codenamed “Vault 7” and released Tuesday by WikiLeaks, reveals that the CIA formed a special unit called the Mobile Development Branch (MDB) to infect smartphones. And within that unit, Apple’s iOS was a prime target.
According to WikiLeaks, the CIA’s MDB developed or exploited a range of hacks, vulnerabilities and even specialized malware to turn iPhones and iPads into spying devices. Compromised iPhones and iPads can track users’ conversations, texts, geolocations and even remotely turn on the camera and microphone.
WikiLeaks’ introduction to the giant cache of leaked CIA files — which at 8,761 documents (so far) is claimed to be the largest in history — says that Apple’s devices were of particular interest to the U.S. spy agency.
Despite iPhone’s minority share (14.5%) of the global smart phone market in 2016, a specialized unit in the CIA’s Mobile Development Branch produces malware to infest, control and exfiltrate data from iPhones and other Apple products running iOS, such as iPads. CIA’s arsenal includes numerous local and remote “zero days” developed by CIA or obtained from GCHQ, NSA, FBI or purchased from cyber arms contractors such as Baitshop. The disproportionate focus on iOS may be explained by the popularity of the iPhone among social, political, diplomatic and business elites.
So-called zero-day exploits are software security holes that are unknown to the software’s publisher — in this case, Apple. They are called “zero day” because they are exploited before they are known, giving the publisher “zero days” to fix it or advise on a workaround.
One of the leaked documents details how the CIA tries to break into new versions of iOS as soon as they get released by Apple. Titled “iOS Triage Process,” it lays out the step-by-step process for cracking a new version of iOS using hacking tools such as Saline, Adderall and Nightvision.
According to another classified document published by WikiLeaks, which serves as a kind of
As well as various zero-day exploits, WikiLeaks says the MDB’s “hacking arsenal” includes malware, viruses and trojans. These “weaponized” exploits allow the CIA (or anyone in possession of the malicious code) to “infiltrate, take control of, and exfiltrate” an iPhone or iPad. In other words, the CIA is able to take control of a device, tap into its guts, and extract communications and data.
The CIA’s capabilities are said to include capturing voice and text communications, identifying the user’s precise geolocation, and turning devices into “covert microphones” by activating the mic and/or camera.
The extra good news is that the CIA’s exploits are said to have already been widely leaked and are circulating among “former U.S. government hackers and contractors.” (That’s how WikiLeaks got hold of the material.)
It’s not clear just how widely circulated the spy agency’s hacking tools have been, but anyone in possession of the code has “the entire hacking capacity of the CIA.” 
The CIA’s org chart shows the specialized Mobile Development Group, charged with spying on smartphones.
Photo: WikiLeaks

The latest Apple/Mac/iOS Pings can be found by searching Keyword "ApplePingList" on FreeRepublic's Search.
If you want on or off the Mac Ping List, Freepmail me
My tv camera is firmly in place in it’s hole, where the CIA gets a great look at my ceiling tiles.
I wonder if Android Blackberry is secure, as I am soon in need of a new phone.
I know far too many people who go out of their way to proclaim their Apple phones and computers are so much better because they are not vulnerable to viruses and other attacks.
And most of these folks consider themselves to be very elite.
I consider myself elite, but my wife disagrees.
Blackberry has pretty much left the phone field. They are now just a software company. There are still a few blackberrys around for sale I guess but there will be no new products anymore. The Priv was probably their last gasp.
They make security software for Android. That’s what I’m wondering about.
Oops my mistake. I was repeating an article I had read the other day about the company but they do seem to have a couple of new phones still. The Keyone and the DTEK60.
I was reading that they actually three phones coming out in 2017, but those phones will be the last if they don’t get traction.
Android Blackberry?
Basically an Android phone using Blackberry security software.
“I wonder if Android Blackberry is secure, as I am soon in need of a new phone.”
I would think BB would have the securest Android devices, but it is running Android, so who knows how much security is possible even with a BB with that software.
So, what is Apple going to do about this?
This really pisses me off.
Probably nothing, unless Apple is going to rewrite their software from the ground up.
Blackphone II from silent circle ..... use a quality VPN, Tor w custom bridges, 12P Bote, Tails and a good AES128 encryption program, stir that with a ROT-13 program and Photon email service out of Switzerland ...... I use it to play chess with my neighbor. Probably drives somebody nuts.
That said never put anything on a IoT gadget you don’t want anyone else to see.
This release gives indications of where any vulnerabilities may lie. Apple will close any it finds. They will also sue the government under the law that requires the government to reveal any known vulnerabilities it knows about so the manufacturer can fix them. This should have been done automatically under that law.
Will these vulnerabilities be fixed by the time iPhone 8 comes out?
correct - Apple will quickly seal the openings. One of their key selling points is security against viruses & hacks. Too much money involved for them.
As for android - it’s open source, extremely prone to hacking and viruses. I got my wife a Android phone ( Galaxy 6) in 2015; 12 months later it was so full of bugs & popup ads that it became useless. Yes, I installed the ad blockers and anti virus programs; useless.
Sold the android and got her a iphone, 7 months later, not a glitch.
I am confident they will be. . . and I think the vast majority of people would never be affected by these vulnerabilities.
I recall that the government could not even open an older model iPhone 5c owned by the San Bernardino terrorists just a year ago. That does not give much credibility to these current claims. That iPhone could have been quietly opened without all that hoopla if what is being claimed now were true about being able to get into a locked iPhone. These agencies were under orders to cooperate and the CIA was brought in, as was the NSA, due to the potential for foreign connections.
I believe they have developed malware that could compromise iOS devices. . . but they have to get it ON the devices. I also believe that they can compromise a device before it is delivered. . . if they have physical possession of it before delivery, which is what was done with Angela Merkel's iPhone. Remote compromising, however, is another issue. I also do not believe they have been paying Apple to maintain any vulnerabilities in iOS, a backdoor, so they can keep their accessibility open as some have hinted. Apple's credibility with the Enterprise and its individual customers is far too valuable to ever agree to such a nefarious arrangement.
Unless that whole episode was a feint to give potential targets a false sense of security.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.