
Posted on 04/12/2016 10:31:56 PM PDT by Swordmaker

Mac users are once again being urged to exercise caution when installing updates to Adobe Flash Player, after a fake update was discovered infecting computers.
Intego security experts have identified the rogue package installer as a variant of OSX/InstallCore, and have updated Intego VirusBarrier definitions to provide protection.

The in-the-wild attack has been spread in the form of a Mac Package installer .pkg file, also known a flat package, and has been signed with a legitimate Developer ID certificate — effectively tricking OS X's built-in Gatekeeper security to believe that the files can be trusted and are not malicious.
Curiously, if the Mac Package installer, called Product.pkg, is located outside the DMG volume and the DMG volume Installer is unmounted, then you will receive a "Missing parameters" error.
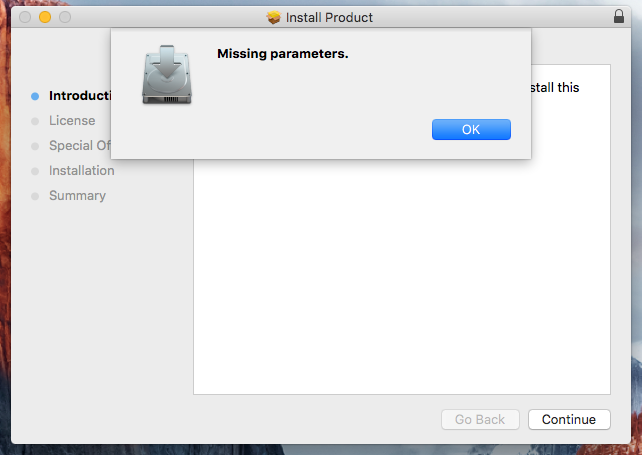
However, if the Package installer is located in the DMG volume, then you will be prompted to continue the installation.

As a result, victims may find that their OS X computers have had a number of potentially unwanted programs (PUPs) installed on their systems. Intego researchers report that third-party apps they have seen being installed by the fake Adobe Flash update include MegaBackup, ZipCloud, and MacKeeper.
Embedded within the installer's code is a copyright message, referencing an Israeli company that develops the InstallCore software installation platform, and has been criticised in the past for "turning a blind eye to malware":
Copyright © 2016 ironSource. All rights reserved.
Two months ago we described how an earlier version of OSX/InstallCore had been spread after Mac users began to see bogus pop-up warnings about Adobe Flash requiring an update, which resulted in scareware being installed onto their computers.
In both this and the previous instance, online criminals signed their malicious code with an Apple developer certificate, allowing the malware to bypass a key part of OS X's built-in defence.
In an attempt to prevent malicious code from infecting OS X computers, by default you are only allowed to run programs that have been downloaded from the official App Store or that have come from "identified developers."
 By using a valid Apple developer certificate, the attackers are tricking OS X into believing that their code can be trusted and allowed to execute — with potentially dangerous consequences.
By using a valid Apple developer certificate, the attackers are tricking OS X into believing that their code can be trusted and allowed to execute — with potentially dangerous consequences.
There are a variety of ways to exploit security holes in OS X Gatekeeper to allow malicious code to sneak onto computers, but presently it seems the simplest method of all is to sign your code with a developer's certificate.
All of which raises the question — from where are the attackers getting their valid Apple developer certificates?
A definite possibility is that some OS X developers are being too careless with their own security, and not recognising the need to properly protect their certificates from hackers.
At the time of writing, the compromised Apple developer ID certificate (MDK7FNV856, in the name of one Nikolay Nikolay Lastovka) has not been revoked.
The seemingly never-ending advisories from Adobe about newly-discovered security holes in Flash Player have made critical updates a regular occurrence. There is a certain irony that security professionals have devoted a lot of time in warning the general public about the importance of installing patches and keeping their Flash installations updated, only to see online criminals exploiting the situation by launching their own attacks as warnings that Flash needs to be updated.
Is it possible that the security of all OS X users is being put at risk because some developers are blind to the threat of their own Macs being attacked, and are carelessly allowing themselves to be hacked and confidential certificates to be stolen?
Ultimately the only safe place to get your Adobe Flash Player update is from Adobe itself, and if you are uncertain — read our guide on how to tell if an Adobe Flash update is valid.
The best advice for many users may be to ensure that you have configured Adobe Flash Player to automatically update itself — while retaining the option to trigger manual updates if you can't wait for Adobe to get around to updating your system.
If you still find the regular appearance of security holes in Adobe Flash disturbing, you may wish to take further action such as uninstalling Adobe Flash completely.

The latest Apple/Mac/iOS Pings can be found by searching Keyword "ApplePingList" on FreeRepublic's Search.
If you want on or off the Mac Ping List, Freepmail me
I aways update from Adobe when It prompts.
Those guys aren’t just hitting Mac....my gosh I had a time there where they were popping up all over the place. Not to mention phone calls from India or Asia.
Interesting. The worst virus I ever got was from an Adobe update. Now, I never update unless I visit the site itself and check the URL rather than just clicking the invite.
Me too! I only update by visiting the site directly.
This is almost as dangerous as installing the real thing.
I never use the invite but instead go directly to Adobe.
How is safe is it to do the automatic update? I never have so just wondering.
I like to wait a week after the new update comes out. That way if they screwed up, I didn’t download it yet.
A distinction without a difference?
The close and minimize buttons are on the left side. Was Steve Jobs left handed? they should be on the right side : )
Thanks, Swordmaker.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.