That story is baseless. Since the Stratfor database was made public, everyone had a copy of it. Anybody could've cracked Paula Broadwell's password, not just Anonymous.
The dumped file is known as "stratfor_users.csv". You can still find it on numerous file sharing and BitTorrent sites. It's 200-megabytes in size, and compresses down to about 40-megabytes. The line you are looking for is the following:
"582458","paulabroadwell@yahoo.com","deb2f7d6542130f7a1e90cf5ec607ad1","paulabroadwell@yahoo.com","0","0","0",,,"1263896967","0","0","1","-18000",,,"paulabroadwell@yahoo.com","a:1:{s:7:\"contact\";i:0;}",NULL,"freelist:152402","0","0",
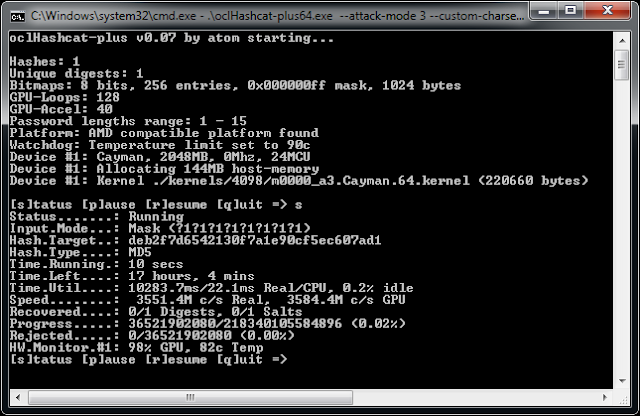
Her email address is in the clear, but the password has been 'encrypted' (into the value deb2f7d6542130f7a1e90cf5ec607ad1) using the MD5 one-way encryption algorithm. You can crack this hash and recover the original password by using a password cracking tool like John the Ripper or oclHashcat. Using oclHashtcat, it'll take 17 hours to crack her password using a GPU accelerator trying 3.5-billion password attempts per second, trying all combinations of upper/lower case and digits.
After doing this, you'll discover the original password is "vsKLVg8L". This is a fairly strong password, consisting of random upper/lower case letters and numbers, which is why it takes 17 hours to crack.
This password is just for her Stratfor account. However, most people re-use passwords, so there is a good chance this was also her Yahoo mail password. If so, then anybody who downloaded the Stratfor dump and cracked the passwords could've logged on and found details of the affair.
I googled her password (https://www.google.com/search?q=vsKLVg8L) and so far, this is the only page that comes up. Hackers often talk about their exploits in public forums. Thus, since her password is distinctive, I half expected the google result come back with hackers discussing her account. I found nothing, which means that if hackers had broken into her email account, they probably weren't the Anonymous types that tend to brag about it.
Update: So why reveal her account and password in this blogpost? Because anybody who would do something bad already knows these details. Time and time again it's been proven that only through full disclosure can we fix things. Ms. Broadwel'sl account and password have been burned, and this is the only way to fully prove just how burned they've become.
Update: This is what oclHashtcat looks like trying to crack the password. As you see, it'll take 17 hours to brute-force eight upper/lower case and digits, even though it tries 3.5-billion passwords/second. I didn't actually run this to completion, because I'd already done this over the entire Stratfor dump last December when it was originally made public. Her password defeated the 'dictionary' and 'mutated dictionary' cracks that got most of the passwords, but not the 'brute-force' crack. Had her password been one character longer, I wouldn't have cracked it.
7 comments:
MD5 isn't encryption. It's an important distinction and what better place than on a security blog to educate people about encryption and hashing.
In my (admittedly unscientific) polling of non-experts, I find they understand "one-way crypto" better than "hash", so that's pretty much how I'm always going to describe it.
Such a random password might be indicative of using a password manager. I'd say it's more likely than not that her Stratfor password was not shared by her e-mail account.
So is the moral of the story to do "sentence passwords"? Like "Iwatchthe11OclockNewsat1030pm"
@political That and not to reuse passwords ever. They are most commonly known as passphrases.
http://en.wikipedia.org/wiki/Passphrase
oclHashcat-lite would be faster. Also you're running a really old version of -plus. Newb ;)
I wonder what an informal poll of your hacker friends would say about how many already had cracked that password.
One thing to note is that password cracking tools aren't guaranteed to give you the actual password but rather a string that hashes to the same value.
Post a Comment