Skip to comments.
Florida sheriff pledges to arrest CEO Tim Cook if Apple resists crypto cooperation LINK
Ars Technica
| March 12, 2016
| by Cyrus Farivar
Posted on 03/12/2016 8:38:30 PM PST by Swordmaker
click here to read article
Navigation: use the links below to view more comments.
first previous 1-20, 21-40, 41-60, 61-71 next last
To: some tech guy
Feds want to play guess the password on a phone belonging to a terrorist.
Phones can be very destructive.
To: some tech guy
Yes, I could. I work with iOS all the time. I’ve been hacking for thirty years.
I can do it. Believe me. And I can recognize a bullsh!tter when I see one. And YOU are one.
iOS has only existed for less than 9 years, oh great hacker of iBS. There was a challenge out there offering $1 million for a hack that could break into an iOS 9 iPhone for the Hacking Team. It went uncollected. No, before you claim it was when they came up with a JAILBREAK, that was not the one I am referring to.
If you are so superior in your abilities, tell us how you would go about it.
22
posted on
03/12/2016 9:08:26 PM PST
by
Swordmaker
(This tag line is a Microsoft insult free zone... but if the insults to Mac users continue..)
To: Vendome
Under what authority, ass hat.Probably if a judge ordered them to in Grady's jurisdiction, dumbass.
23
posted on
03/12/2016 9:08:59 PM PST
by
VeniVidiVici
(Obama = ISIS Fanboy)
To: Swordmaker
Grabs popcorn, i cant wait to read the reply.
24
posted on
03/12/2016 10:13:45 PM PST
by
Ainast
To: Ainast
Grabs popcorn, i can't wait to read the reply. Make lots of popcorn. I suspect you are going to have a long wait.
25
posted on
03/12/2016 10:22:56 PM PST
by
Swordmaker
(This tag line is a Microsoft insult free zone... but if the insults to Mac users continue..)
To: Swordmaker
What an idiot. This is still under litigation. I’d like to see him try. I hear Apple even has attorneys on staff.
26
posted on
03/12/2016 10:30:22 PM PST
by
DesertRhino
("I want those feeble mined asses overthrown,,,")
To: dp0622
“He’s liable to end up having gay sex.”
Hear a lot of homo jokes about that CEO. It would make sense if the Government was some paragon of heterosexuality. But the government is the leading advocate for homosexuality in the nation. There are probably fags on the FBI team and in the US Attorneys office pushing this.
So its offsetting penalties and get back to the actual arguments in the case.
27
posted on
03/12/2016 10:34:10 PM PST
by
DesertRhino
("I want those feeble mined asses overthrown,,,")
To: Swordmaker
ROTFLMAO. I am going to get popcorn too.
28
posted on
03/12/2016 10:34:47 PM PST
by
BullDog108
(A Smith & Wesson beats four aces!)
To: VeniVidiVici
“Probably if a judge ordered them to in Grady’s jurisdiction, dumbass. “
He can issue a search warrant under the 4th amendment. He cannot contact a company and compel them to create a product, break a security feature of their product, and to do the work of the FBI for them. Dumbass.
I know its complex, but if the FBI has a warrant from a judge to search your safe. You do not have to unlock your front door, secure the dogs, or turn off your alarm. The safe manufacturer cannot be ordered to the scene to find a way to open the lock.
The FBI could bring drills, saws, cutting torches, Vinnie the safecracker, etc. A warrant only gives them permission to seize and search, not to compel anyone to come do their work for them.
The FBI has seized the phone, and they may search it. That’s what a warrant allows. Dumbass.
29
posted on
03/12/2016 10:42:34 PM PST
by
DesertRhino
("I want those feeble mined asses overthrown,,,")
To: some tech guy
The phone is encrypted. Please, tell me how you can decrypt the cypher without the keys? If there’s no software on the phone that knows what the keys are how can this be done? Even if there is software on the phone that knows the keys it would also need to be able to be remotely triggered to go through a decryption process. This doesn’t exist.
You’re wrong. If you were right this “problem” wouldn’t exist, I’m sure there would be many others able to accomplish the same thing. Unless you’re the worlds greatest genius.
30
posted on
03/13/2016 1:49:23 AM PST
by
fuzzylogic
(welfare state = sharing consequences of poor moral choices among everybody)
To: bigbob
???? Are you at the wrong site?
31
posted on
03/13/2016 1:50:22 AM PST
by
fuzzylogic
(welfare state = sharing consequences of poor moral choices among everybody)
To: some tech guy
32
posted on
03/13/2016 1:51:46 AM PST
by
Repeal The 17th
(I was conceived in liberty, how about you?)
To: bigbob
Water board that rascally iphone. Meanwhile looks like Tim Cook better avoid foam parties in this Florida jurisdiction.
33
posted on
03/13/2016 1:54:05 AM PST
by
dennisw
(The first principle is to find out who you are then you can achieve anything -- Buddhist monk)
To: Swordmaker
Polk County Sheriff Grady Judd, for those who are asking “who? where?”
34
posted on
03/13/2016 4:30:37 AM PDT
by
NonValueAdded
(Buchanan: A note of caution: This establishment is not going quietly.)
To: fuzzylogic
OK, I’m back after several hours hacking iPhones.
So, I’m going to admit I was wrong. I can’t do it. Not in the scenario given. I’ll give the reasons why, which hopefully some will find interesting.
Now, I never intended to claim I can crack AES, that would be a very stupid claim to make. AES is rock solid, and I know this as the HIPAA expert at my company. It’s gold standard encryption. Especially the FIPS140-2 variant of AES256, which means it’s been certified.
My attack vector requires access to a phone *backup* on a desktop computer. With that, I can load it into the iPhone simulator, hack the code on that to stop the check on number of incorrect passcode entries, and fire sequences of PINs at it until it spits out the right result. This works; I just tried it.
HOWEVER, and this is where I admit defeat, with just the phone, the hardware won’t play. I can hack the software, but without physically removing the crypto chip, shaving the surface off and reverse engineering it (a process which is possible, but will cost a couple of hundred thousand bucks and could well just break the chip), it isn’t possible. You’d have to do that to get the AES key, which is what you need to decrypt.
So, I am wrong and I apologize to Swordmaker. I gave it my best college try and failed.
35
posted on
03/13/2016 4:36:34 AM PDT
by
some tech guy
(Stop trying to help, Obama)
To: some tech guy
I’m going to add some more to this because I’m amped up after hours of trying it.
That crypto chip is a work of art. Apple really, really thought about this. I figured I could bypass it with some clever hacks, but it’s simply not possible.
For a little while I even had the phone plugged in to some electronics to try to grab stuff of its internal bus, but EVEN THAT isn’t enough to bypass the chip. Sure, I could stop the flash erase, but that doesn’t help without access to the AES key - I *have* to have the key to decrypt.
If I were the NSA with unlimited cash I’d attempt the chip shave, but that’s the only way I can see this working.
I made a strong claim, tried to back it up, and failed. More fool me.
36
posted on
03/13/2016 4:46:31 AM PDT
by
some tech guy
(Stop trying to help, Obama)
To: some tech guy
and ... one more.
Not even Apple can hack this, unless they have a backdoor to the cypto chip. Just altering the software won’t allow unlimited PIN entry, and I can state that as fact because it’s what I’ve been trying. It’s the hardware which blocks you.
37
posted on
03/13/2016 4:57:34 AM PDT
by
some tech guy
(Stop trying to help, Obama)
To: Swordmaker
Ah, the never-camera-shy Grady Judd.
38
posted on
03/13/2016 5:30:26 AM PDT
by
tbpiper
To: some tech guy
Thanks for looking into it. The second part of you original claim was correct, the case is not about tech but judicial precedent. But as you just noted, the tech is rapidly making the whole argument moot. Either Apple and every other vendor of (e.g.) FIPS 140-2 will be mandated by a real law to have a back door in every device or they won't and there's no court order or writ or warrant in the world that will make the device give up its data.
I think you ran into was the SoC used to take the passcode, check it against the hash, combine with the UID and create the decryption key that decrypts the AES key. Note that the OS (and RAM and main processor) can be untrustworthy in this system and you proved that by not being able to get the AES key. I wouldn't rule out the NSA shaving down the SoC and reading the passcode hash, but at that point they have probably destroyed the UID and they need both to recover the AES key. Here's a picture of the system (probably):
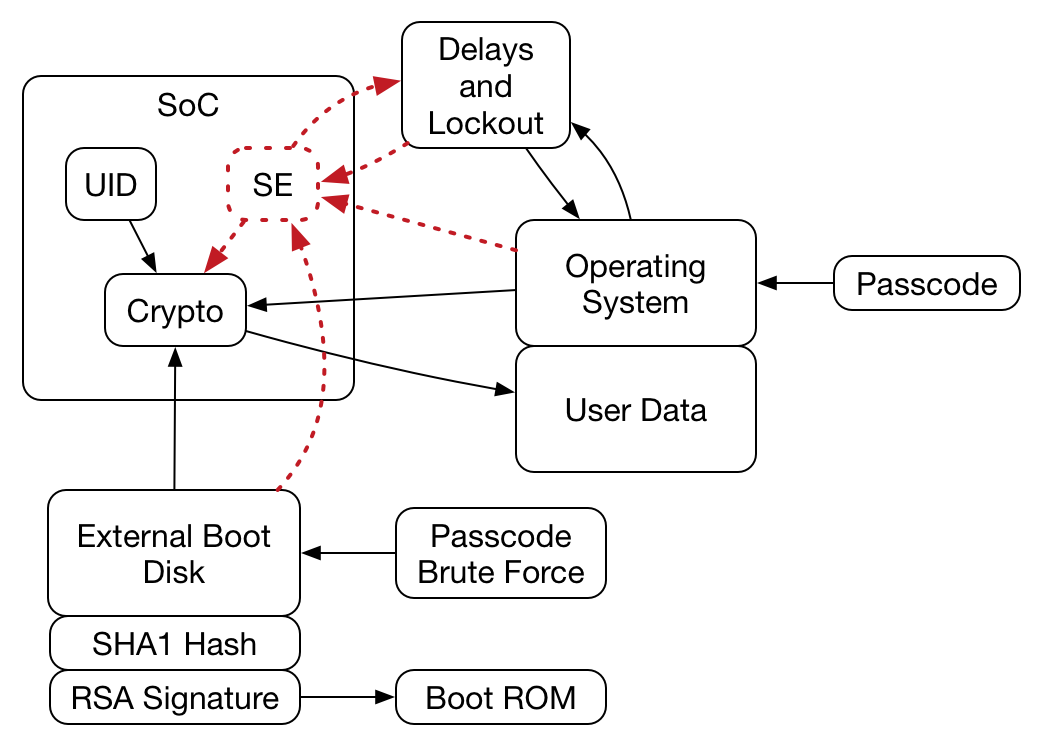
Note that with your nearly complete control of everything going on outside of the SoC you had no way to obtain the AES key.
39
posted on
03/13/2016 5:58:19 AM PDT
by
palmer
(Net "neutrality" = Obama turning the internet over to foreign enemies)
To: palmer
That’s a great diagram.
Yes, the problem was that I couldn’t get the key. I was hoping that with a bus dump I could either 1) get the UID and guess the algorithm (failed) or 2) The SoC was stupid enough to write incorrect guess count to flash (it’s not)
No, Apple really thought about this, and I’m genuinely impressed. Even with a shave it’d be very hard.
Everything which is insecure is not trusted in this system, which is a great way of doing things.
40
posted on
03/13/2016 6:21:17 AM PDT
by
some tech guy
(Stop trying to help, Obama)
Navigation: use the links below to view more comments.
first previous 1-20, 21-40, 41-60, 61-71 next last
Disclaimer:
Opinions posted on Free Republic are those of the individual
posters and do not necessarily represent the opinion of Free Republic or its
management. All materials posted herein are protected by copyright law and the
exemption for fair use of copyrighted works.
FreeRepublic.com is powered by software copyright 2000-2008 John Robinson
