To: some tech guy
I’m going to add some more to this because I’m amped up after hours of trying it.
That crypto chip is a work of art. Apple really, really thought about this. I figured I could bypass it with some clever hacks, but it’s simply not possible.
For a little while I even had the phone plugged in to some electronics to try to grab stuff of its internal bus, but EVEN THAT isn’t enough to bypass the chip. Sure, I could stop the flash erase, but that doesn’t help without access to the AES key - I *have* to have the key to decrypt.
If I were the NSA with unlimited cash I’d attempt the chip shave, but that’s the only way I can see this working.
I made a strong claim, tried to back it up, and failed. More fool me.
36 posted on
03/13/2016 4:46:31 AM PDT by
some tech guy
(Stop trying to help, Obama)
To: some tech guy
and ... one more.
Not even Apple can hack this, unless they have a backdoor to the cypto chip. Just altering the software won’t allow unlimited PIN entry, and I can state that as fact because it’s what I’ve been trying. It’s the hardware which blocks you.
37 posted on
03/13/2016 4:57:34 AM PDT by
some tech guy
(Stop trying to help, Obama)
To: some tech guy
Thanks for looking into it. The second part of you original claim was correct, the case is not about tech but judicial precedent. But as you just noted, the tech is rapidly making the whole argument moot. Either Apple and every other vendor of (e.g.) FIPS 140-2 will be mandated by a real law to have a back door in every device or they won't and there's no court order or writ or warrant in the world that will make the device give up its data.
I think you ran into was the SoC used to take the passcode, check it against the hash, combine with the UID and create the decryption key that decrypts the AES key. Note that the OS (and RAM and main processor) can be untrustworthy in this system and you proved that by not being able to get the AES key. I wouldn't rule out the NSA shaving down the SoC and reading the passcode hash, but at that point they have probably destroyed the UID and they need both to recover the AES key. Here's a picture of the system (probably):
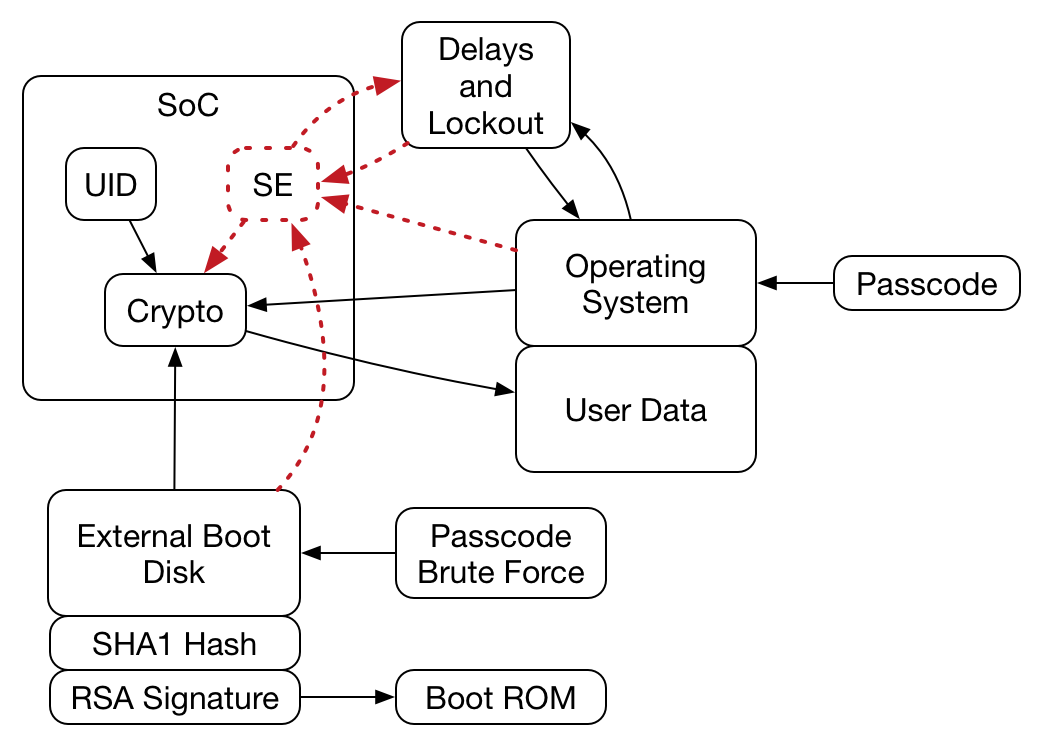
Note that with your nearly complete control of everything going on outside of the SoC you had no way to obtain the AES key.
39 posted on
03/13/2016 5:58:19 AM PDT by
palmer
(Net "neutrality" = Obama turning the internet over to foreign enemies)
To: some tech guy; Swordmaker
More fool me. I must disagree. You made a foolish claim, yes. But, you were man enough to back down when you found out the claim was foolish.
You are not a fool. Thank you for being honest in your results, FRiend.
55 posted on
03/13/2016 8:48:57 AM PDT by
MortMan
(Let's call the push for amnesty what it is: Pedrophilia.)
To: some tech guy
I made a strong claim, tried to back it up, and failed. More fool me. No, Tech guy, I wouldn't call you a fool. You have learned something. The fools are those who refuse to learn and admit their failures. You are wise. I learned to avoid this years ago. Don't be surprised if you get attacked by the fools now.
62 posted on
03/13/2016 11:11:37 AM PDT by
Swordmaker
(This tag line is a Microsoft insult free zone... but if the insults to Mac users continue..)
To: some tech guy
Holy sh!t. You really, REALLY gave it your all attempting to back up your claim, complete with easily understandable technical explanations of every step. I give you massive props for putting your money where your mouth is.
FreeRepublic.com is powered by software copyright 2000-2008 John Robinson
