Posted on 03/07/2019 7:50:15 PM PST by bitt
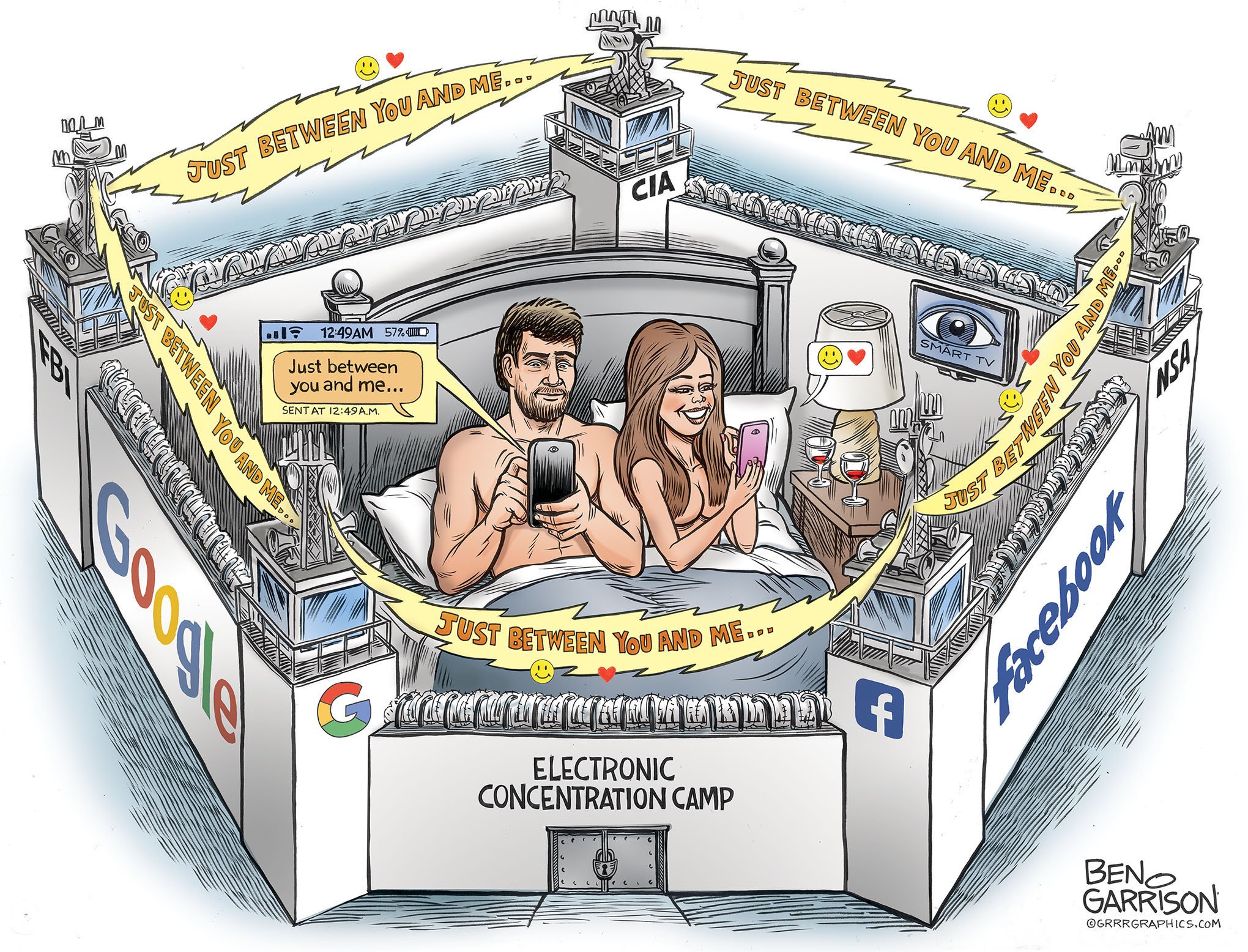
A function of Intel's processors dealing with speculative execution has another vulnerability that affects all Intel-based computers including Apple's Mac, researchers have revealed, with "Spoiler" potentially allowing an attacker the ability to view the layout of memory, and in turn potentially access sensitive data stored in those locations.
The speculative execution function of Intel's processors, used to increase the performance of a CPU by predicting paths an instruction will go through before the branch is completed, is a useful function but one that has caused Intel issues in the past. A new report from security researchers from Worcester Polytechnic Institute and the University of Lubeck published on March 1 indicates there's another issue that needs to be fixed.
Dubbed "Spoiler," the technique is able to determine how virtual and physical memory is related to each other, by measuring the timing of speculative load and store operations performed by the processor, reports The Register. By spotting discrepancies in the timing, it is possible for an attacker to determine the memory layout, and in turn know areas to attack.
"The root cause of the issue is that the memory operations execute speculatively and the processor resolves the dependency when the full physical address bits are available," researcher Daniel Moghimi advised to the report. "Physical address bits are security sensitive information and if they are available to user space, it elevates the user to perform other micro architectural attacks."
(Excerpt) Read more at appleinsider.com ...
P
Billions of transistors, all off on their own, doing whatever.
What could possibly go wrong?
Can’t tell the bugs from the features...
Sounds like a lot of work beyond my capability to breach someone’s system. I’ll wait till the AAP comes out.
Thanks for the memories.
Need the “Executive Summary” in ENGLISH, Please.
Not all Freepers are software geeks!
Well, in 2020 Apple will supposedly stop using Intel chips.
Until then....
/s

P
I was taught that ALL bugs are FEATURES!
Bill Gate$ says.......
Spoiler Alert.
Will there be a recall and of course refunds? /sarc
I AM a GEEK. My job used to be to extend the sample BIOS supplied by Intel to take advantage of new Reliability And Serviceability (RAS) features for the three operating systems which run on the servers manufactured by my company.
“Physical address bits are security sensitive information and if they are available to user space, it elevates the user to perform other micro architectural attacks.”
There must be something else going on here, because this doesn’t make sense to a geek.
It wouldn’t be the first time that the technical writer scrambles the message. But the capability described above wouldn’t make me lose any sleep.
I recall the Clinton Administration being said to have wanted bugs like these.
Engineers etc are rarely required to actually learn how to write good. *nudge*wink*
Greeeat. Do I need to wait for the next scam call from “Hardeep” (AKA “John”) addressing this problem?

In theory the user mode code could include javascript that you loaded simply by visiting a website. But I am pretty sure a javascript exploit will never come to fruition. Not only that, but a browser can defend against such an attack rather easily by small randomizations in javascript execution.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.